DDoS Mitigation Service
Defend your organization against cyber-attacks.
What is a DDoS Attack?
DDoS attacks are Denial-of-Service attacks that leverage the massive, distributed, and stolen computing power from infected endpoints to flood target networks and web applications with traffic. The goal of DDoS attacks is to make an organization’s online service unavailable by overwhelming it with traffic from multiple sources. DDoS attacks are designed to target any aspect of a business and its resources, and can easily disable a specific computer, service or an entire network.
Over the recent years, DDoS attacks have evolved in strategy and tactics. DDoS attacks fall into three broad categories depending on which area of the customer’s network infrastructure the attack is focused.
Volumetric attacks
cause congestion at the customer network by sending too much traffic into the network so that it overwhelms the bandwidth of the network. These attacks are typically executed using botnets, an army of computers infected with malicious software and controlled as a group by the hacker.
State Exhaustion attacks
focus on actual web servers, firewalls and load balancers to disrupt connections, resulting in exhausting their finite number of concurrent connections the device can support. As a result, the genuine users trying to access data from the customer’s site will not be able to do so.
Application layer attacks
also known as Layer 7 attacks, specifically target weaknesses in an application. These sophisticated threats are harder to detect because not many machines are required to attack, generating a low traffic rate that appears to be legitimate. This results in genuine users not being able to access the applications residing at the customer site.
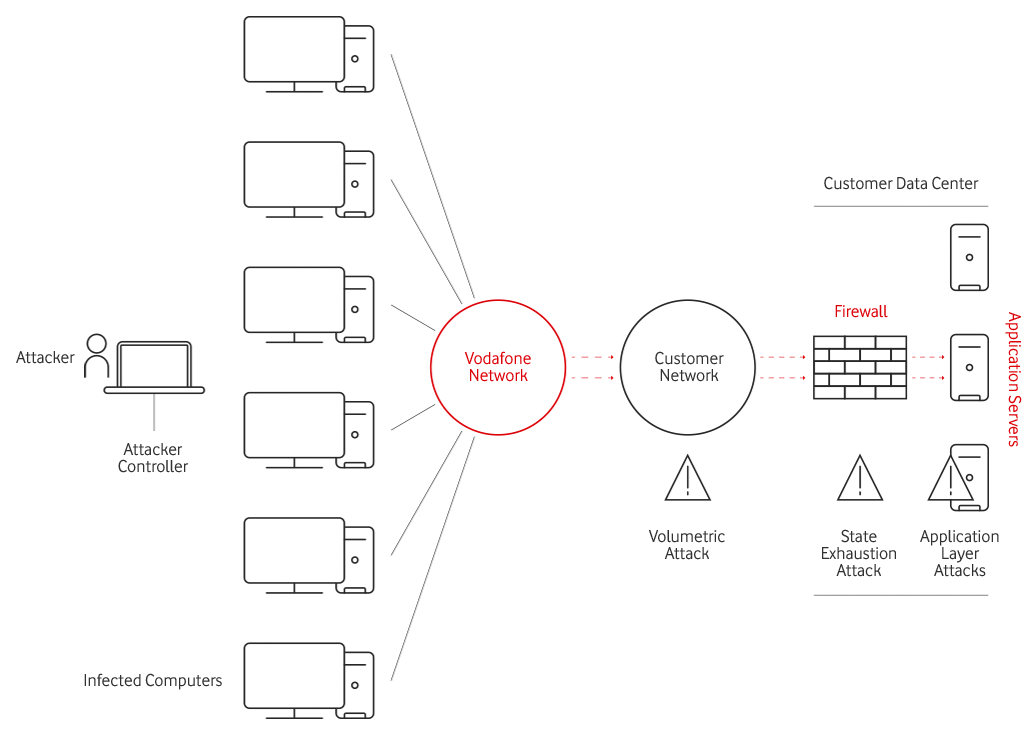
DDoS Mitigation Service - What is it?
The end-to-end DDoS mitigation proposition will provide assured connectivity to dedicated internet customers, enabling safer communications over the internet. Since today’s attacker uses a combination of volumetric, state-exhaustion and application-layer attacks to execute multi-vector DDoS attacks – a layered approach is by far the most effective. Industry best practices have proven the following in terms of dealing with DDoS:
Volumetric DDoS protection is deployed within the core of Vodafone’s Internet network.
The equipment deployed at the customer premise will take care of the mitigation of Layer 4 to Layer 7 DDoS attacks. This enables customers the ability to provide immediate always-on DDoS detection and mitigation to protect their applications and network infrastructure from state and application DDoS attacks.
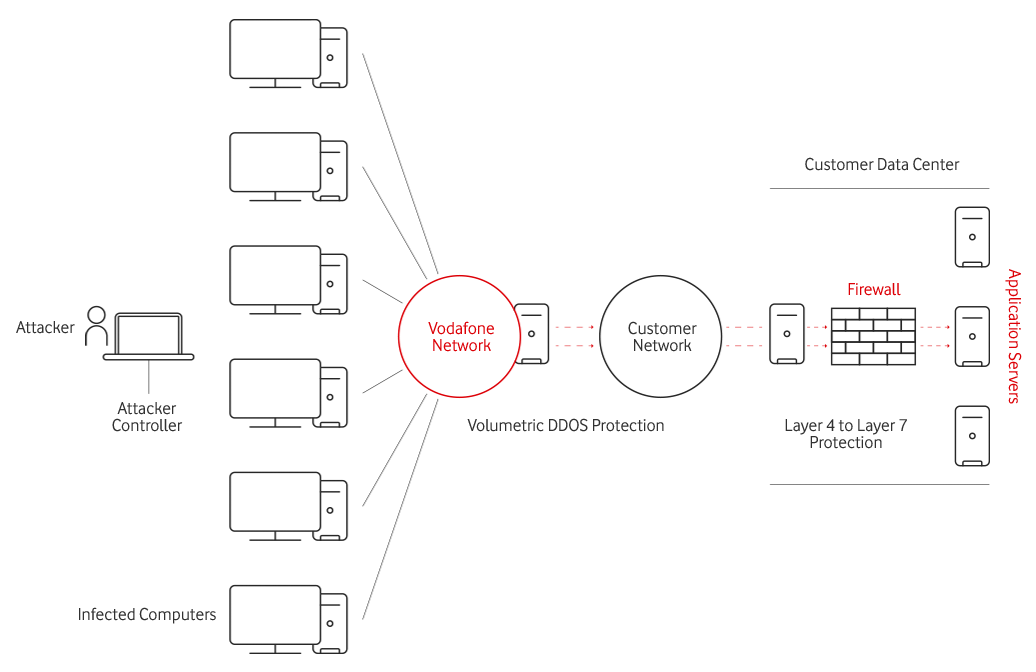
Measurable Return on Investment with Vodafone DDoS Mitigation Service
DDoS attacks disrupt operations and prevent users from accessing critical Web applications
This downtime results in loss of productivity, loss of visitor traffic, loss of e-commerce transactions, revenue loss, impact to competitive position, negative brand impact, loss of reputation, reduction in share price, loss of business data, rise in IT expenditure to defend from attacks.
The value of these lost opportunities will vary across businesses and industries However, businesses can and should measure the potential damages that a DDoS attack can cause in terms of dollars per hour.
For some financial and web-based businesses, DDoS attacks can result in millions of dollars of damages per hour
Why Vodafone DDoS Mitigation Service?
90% of businesses believe that maintaining security and privacy in a highly connected world is a business imperative
78% of businesses believe their current IT and communication facilities are not able to effectively manage security and access control
-
Traditional Internet security is ineffective
-
Existing defenses are easily overwhelmed by large attacks
-
Increasing sophistication and size of attacks are hard to counteract
-
Limited budgets and resources to dedicate to self-operated systems
DDoS Mitigation Service – Technical Description
The service will have DDoS protection mechanisms to offer the following features:
Blocking of volumetric attacks at Layer 3 of the OSI layer
Blocking of state-exhaustion and application attacks at layer 4 to layer 7 of the OSI layer
Protection from:
- Flood Attacks (TCP, UDP, ICMP, DNS, SSDP, NTP, SNMP, SQL RS, Chargen Amplification, DNS Amplification, Microsoft SQL Resolution Service Amplification, NTP Amplification, SNMP Amplification, SSDP Amplification)
- Fragmentation Attacks (Teardrop, Targa3, Jolt2, Nestea)
- TCP Stack Attacks (SYN, FIN, RST, SYN ACK, URG-PSH, TCP Flags)
- Application Attacks (HTTP GET floods, SIP Invite floods, DNS attacks, HTTPS protocol attacks)
- DNS Cache Poisoning, Vulnerability attacks, Resource exhaustion attacks (Slowloris, Pyloris, LOIC, etc.)
- Flash crowd protection
- IPv4 and IPv6 attacks hidden in SSL encrypted packets
The service you can count on
24/7 Service Operating Centre with dedicated team for fixed and integrated services and Dedicated Account Manager
For further information please contact your Account Manager or request for a call back here
